NTP Fingerprinting with nmap
NTP - An easy, quick, reliable and lightwight way to fingerprint a system
About ten years ago, and around three years after the nmap scripting engine (NSE) made it into mainline, I wrote and contributed ntp-info to the nmap project.
Back in 2009 there weren’t a lot of NTP fingerprinting tools around which you could easily extend and add to your own cli based toolchains. So I decided to give NSE (lua) scripting a spin and wrote the ntp-info script. Instead of repeating myself please have a look at the description from the code:
|
|
You can get the full code on the nmap github. It ships with nmap by default (if installed with scripts) and runs if UDP and service identification scans, or script scans, are performed and UDP port 123 is detected as open or open|filtered. This is how a simple run looks like:
# nmap -sU -p 123 -PN --script=ntp-info time.google.com 9X.XXX.XXX.X4
Starting Nmap 7.60 ( https://nmap.org ) at 2019-04-20 13:14 BST
Nmap scan report for time.google.com (216.239.35.12)
Host is up (0.011s latency).
Other addresses for time.google.com (not scanned): 216.239.35.0 216.239.35.4 216.239.35.8
rDNS record for 216.239.35.12: time4.google.com
PORT STATE SERVICE
123/udp open ntp
| ntp-info:
|_ receive time stamp: 2019-04-20T12:14:20
Nmap scan report for 9X.XXX.XXX.X4
Host is up (0.061s latency).
PORT STATE SERVICE
123/udp open ntp
| ntp-info:
| receive time stamp: 2019-04-20T12:14:15
| version: ntpd 4.2.0-a Fri Mar 30 13:07:53 2018 (1)
| processor: i386
| system: FreeBSDJNPR-10.3-20180310.ba55661_buil
| leap: 3
| stratum: 16
| precision: -22
| rootdelay: 0.000
| rootdispersion: 3868.605
| peer: 0
| refid: INIT
| reftime: 0x00000000.00000000
| poll: 4
| clock: 0xe0658b8c.c27ffba3
| state: 1
| offset: 0.000
| frequency: -41.838
| jitter: 0.000
|_ stability: 0.000\x0D
Service Info: OS: FreeBSDJNPR-10.3-20180310.ba5566
Nmap done: 2 IP addresses (2 hosts up) scanned in 10.96 seconds
And if you ever wondered how various intel / fingerprinting services on the interwebs do NTP fingerprinting I got this for you:
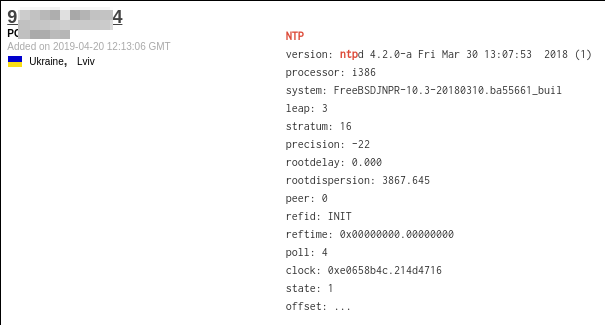
Let me know if you have any questions, feedback or general comments in the respective twitter thread over here:
https://twitter.com/mytty_project/status/1119589125055832064